Reporting a Security Breach
Western's Security Breach Protocol has been developed by the Bank Card Committee in accordance with PCI DSS. Below are the process that Merchants must follow in the case of a suspected security breach to their PCI envrionment. The Security Breach Protocol can be found at the bottom of this page and Merchants must have this document easily accessible for all employees in the case of a security breach.
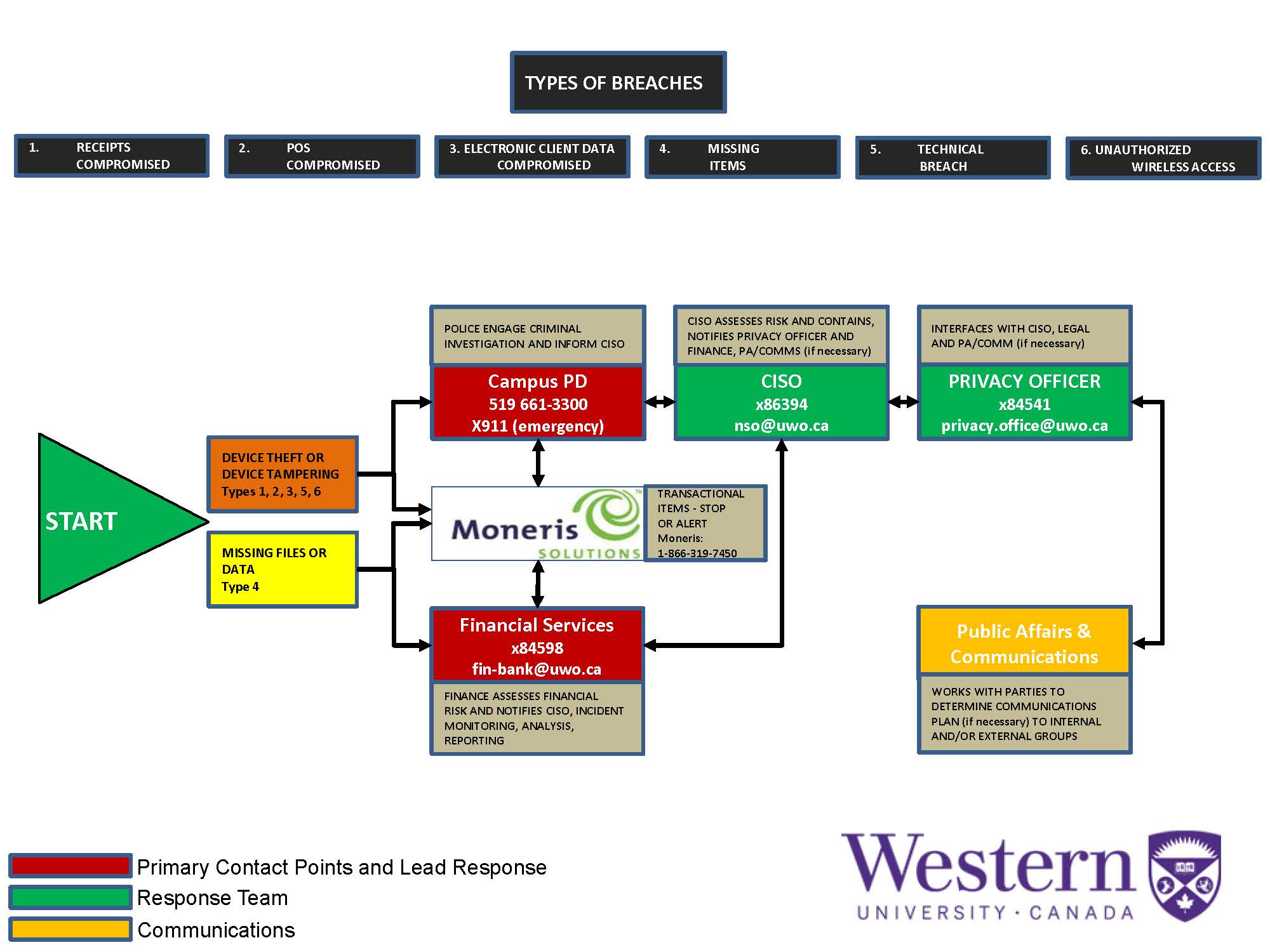
Merchants must follow these steps in the case of a suspected breach to their PCI environment.
Step 1: Identifying the Type of Breach
1. Forms or Documentation Compromised
If forms and documentation related to a commercial transaction have been tampered with, accessed inappropriately, or removed without consent, Western's Security Breach Protocol should be followed.
2. Point of Sale (POS) Device(s) Compromised
If the Merchant suspects that POS device(s) have been tampered with, Western's Security Breach Protocol should be followed.
3. Electronic Client Data Compromised
If at any time the Merchant suspects that internal systems have been accessed inappropriately or if the Merchant suspects that data might have been altered, deleted, or compromised, Western's Security Breach Protocol should be followed.
4. Missing Items
In the case where forms or documentation has gone missing, paperwork has been misplaced, or records are absent from a data system and the Merchant does not think that a compromise has occurred, Western's Security Breach Protocol should be followed.
5. Technical Breach
If the Merchant suspects a data system has been breached or has been targeted for hacking, Western's Security Breach Protocol should be followed.
6. Unauthorized Wireless Device
Similar to the Technical Breach, if the Merchant suspects that there is an unauthorized technology component present in the PCI environment, Western's Security Breach Protocol should be followed.
Step 2: For Items 1, 2, 3, 5 and 6
If theft or tampering is involved the Merchant should contact Campus Safety and Emergency Services (911 when on campus).
Please contact the payment processor (the Merchant will need to provide LOCATION and the SERIAL NUMBER of the device if applicable).
Step 3: For Item 4
If theft or tampering is not involved, the Merchant must obtain all details and contact the payment processor (the Merchant will need to provide LOCATION and the SERIAL NUMBER of the device if applicable).
Western Financial Services must also be notified (Financial Services - Banking or 84598.)
Step 4: Follow Up as Needed
Campus Safety and Emergency Services, Central Information Security Officer (CISO), the Bank Card Committee and Western Financial Services will follow procedures and notify personnel accordingly.
Once the security breach is properly reported, the Merchant must complete a Post Reporting Incident Response Form.